Faith, Trust and Pixie Dust
Erik Boss
2017-10-12
Who even is this guy?

- Erik Boss
- ECRYPT-NET ESR #6
- Ruhr-Universität Bochum
- EMSEC
(In)famous for
- Strong language
- Bad jokes
- Awesome surname (thanks Dad)
And what is he doing here?
- Microcode for Good (TM) & Evil (TM)
- Lawful Evil for now
- Good (TM) later
- Ignoring common sense
What is this microcode you speak of?
"It's really small…"
– Captain Obvious
But really…
"That thing that gets updates whenever Intel/AMD messes up."
- The lowest of levels of software programming
- Anything lower is basically hardware
- Implements the ISA
- Most CPU architectures seem to include some form of microcode
Silly example
pop [ebx]
can be implemented in microcode as
load tmp, [esp] store [ebx], tmp add esp, 4
Why though?
"To err is human."
- Flexibility both in design and after deployment
- Disable/fix faulty instructions
Case in Point
"8.9999163362: It's Close Enough, We Say So"
– S. Sadi Seferoglu
(But many more…)
But how does it work?

Thank the gods for these guys

(Note: this is for slightly older AMD CPUs)
Nitty gritty
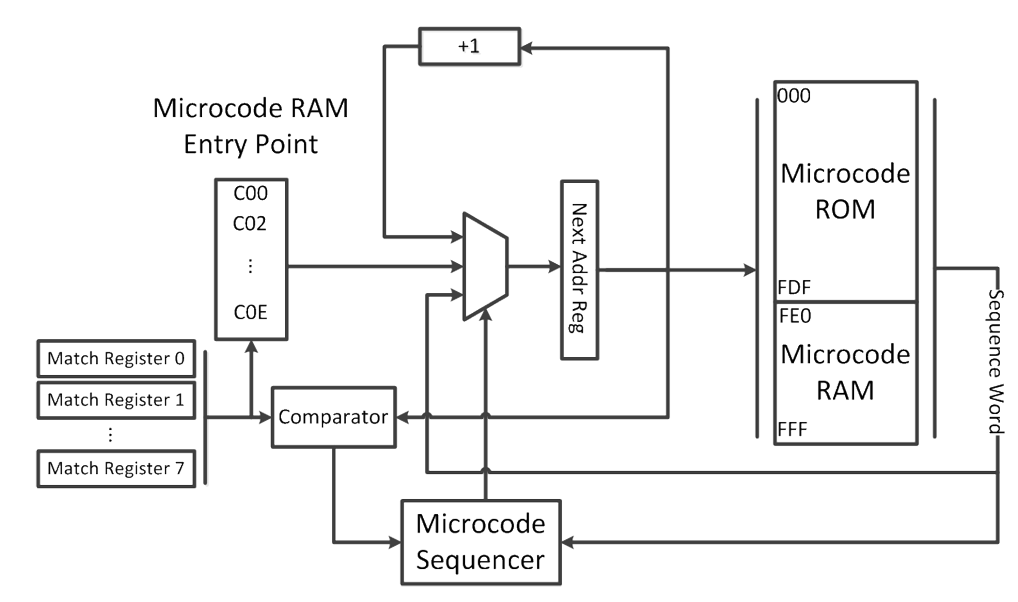
For Evil (TM)
"Come to the dark side. We have cookies."
– Darth Vader
How do we exploit this for lawful evil purposes?
Channeling Odysseus

"Toy example"
- Hook
div - Preserve semantics in normal operation
- Something "a little extra" on a given trigger
div Trojan
/* The instrumented div instruction... */ if (eax == 0xA && ebx == 0xB) { eip += 1 } else { /* normal reg32 div */ }
; Pulling the trigger... mov eax, 0xA mov ebx, 0xB div ebx add eax, 0xcc909090 ;payload
; Leading to... mov eax, 0xA mov ebx, 0xB div ebx /* skip */ nop nop nop int3
World's most i(NSA)ne threat model
If nation-state adversaries are not your problem, microcode Trojans are not going to be either.
– Me

Probably… Maybe… Hopefully
For Good (TM)

Let's think about this…
- Vendor-certified cryptographic (or other) primitives
- Distinct sets of extensions?
- Easier than re-configurable hardware?
- We could have both
State of the nation

Two open evaluation microcoded RISC-V platforms
- One modeling a smaller embedded device
- The other a "normal" CPU capable of running interesting things
- Linux?
- Based on cores from http://0pf.org/
Wibbly wobbly timey wimey
Short Term
- Finalize both evalution platforms
- Run the attacks on a bunch of crypto
- …
- Profit
The Future is Now
"No it's not."
– Some sane person
Long Term
- Implement cryptographic primitives in microcode?
- More interesting Trojans?
- Attacks in noisier environments?
- Attack non-cryptographic security-critical systems?

Questions?
(Better, check out: https://youtu.be/I6dQfnb3y0I)